Licensing Service Development for 3D Printers
Background
Licensing protects developers' copyrights, ensures product quality, and encourages innovation since developers are more likely to invest time and money in creating new products when fairly compensated for their work.
Subscription can be considered a type of licensing. This model entitles clients to use the product for some time in exchange for a regular fee. In this project, we were tasked with developing such a licensing service.

Request
A while back, our team participated in developing a 3D printer. At some point, the customer had to decide how to distribute the ready-made product. He chose to sell it by subscription.
Integra Sources’ job was to design and create a licensing service and its components that could block and unlock device functions depending on subscription terms.
Solution
System composition
The system consists of three elements: a web server, a desktop application for activating licenses, and a microcontroller on the device.
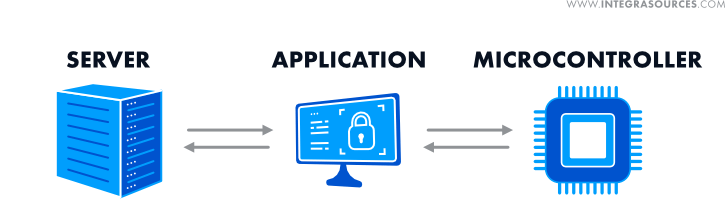
1. Desktop application
Our team had developed a cross-platform app for the customer’s product during our previous work on this project. The application enables users to control and configure the device. The app was written in C++ using the Qt framework. When developing the licensing solution, we expanded the functionality of the app so that it could be used to activate licenses.
The application acts as an intermediary between the device (its microcontroller) and the web server. It provides a license key input field and transmits device data to the server, allowing users to activate the license.
2. Microcontroller
It validates the digital signature contained in the license structure and provides access to device features in accordance with the subscription plan the buyer paid for. The development of the microcontroller firmware was delegated to another team. However, Integra kept in touch with them to coordinate work.
3. Web server
The server is a web application that generates license keys and stores license data, device data, a subscription plan, and other information. It was created with the Jmix framework.
Jmix is a platform for rapid web application development in Java. It uses the declarative paradigm and offers a wide selection of pre-built components, so creating apps in Jmix takes less time and, therefore, is cheaper. In addition, Jmix supports modern web technologies such as HTML5, CSS3, and JavaScript, which allows for creating applications with a visually appealing and intuitive GUI. At the same time, the framework is based on Java and Spring Framework, which ensures high scalability and performance.
We had to adjust certain interface elements in accordance with the specifics of the program: it required extra checks before information could be added into the database. Therefore, we had to customize the interface directly in the programming code in Java.
Using the capabilities of the Jmix HTTP server in Java, we developed a separate module for providing license data to client applications. The module implements the REST API protocol for servicing HTTP requests. It was built into the Jmix HTTP server.
The team also developed protocols for communication between the desktop application and the device, as well as between the app and the server.
Licensing Process
The licensing mechanism was structured as follows.
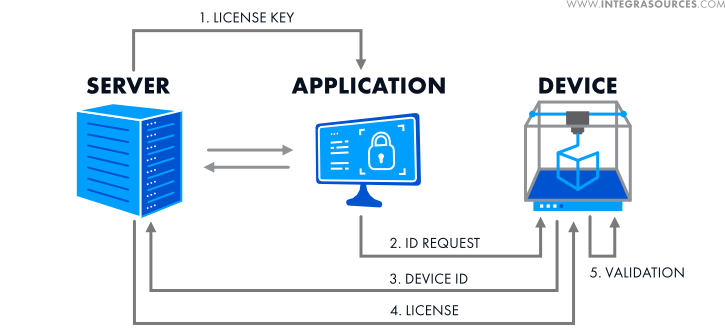
1. When subscription payment is confirmed, the user’s application receives a license key. The key represents the row number in the database containing the license and device information.
2. After receiving the license key, the desktop application requests the device microcontroller for its serial number, product type, and current firmware version. This information serves as the ID of the device.
3. This information is sent to the web server and entered into the database.
4. The server generates a license structure based on this data. The license contains subscription data and information about the device for which it is issued, signed with a digital signature (hash value). The license can only activate the device whose ID was transferred to the server. Even if hackers intercept the digital signature, it cannot be used to activate another device. The license is then transferred through the app to the device.
5. The device microcontroller validates the license. If the digital signature is genuine, the microcontroller unlocks the corresponding functions on the device for the period chosen by the buyer. To ensure that the license cannot be reused after expiring, the device has a built-in clock. The time is compared to the license start and end dates from the license data.
How the license is validated
We decided to use the SHA-256 hashing algorithms for license verification. This algorithm uses a hash function that converts any message or data into a fixed-length sequence of symbols called a hash value, or checksum. Hashing has the following features:
1) Identical input data results in identical hash values.
2) Checksums have a fixed length regardless of the size of the input data.
3) Hashing is a unidirectional process. Any message can be converted into a hash value, but it is impossible to calculate the input data from the hash value.
4) Even minimal changes in the input data result in a completely different checksum.
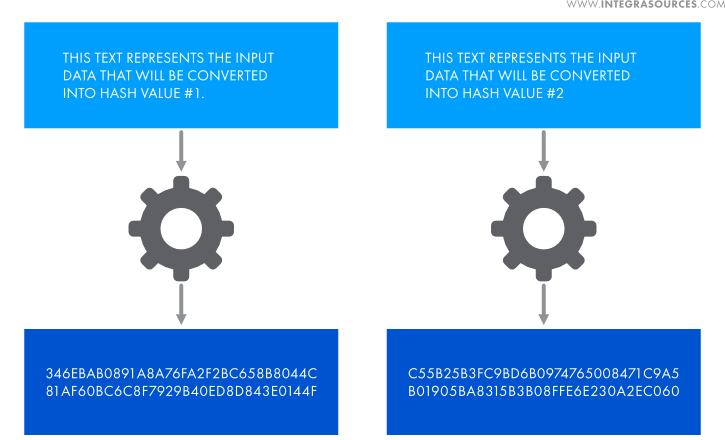
In this project, part of the input data, from which the checksum is calculated, is stored on both the server and the device. When the server forms a license structure, this data is hashed and the resulting digital signature is sent to the device. The device, in turn, uses the same algorithm to calculate a hash value from the data stored on it. Since the input data on the server and the device are identical, the resulting checksums should be identical as well. If the microcontroller detects a mismatch, this means that the digital signature was forged.
One of the vulnerabilities of hashing algorithms is the probability of collisions. Collisions happen when two different messages generate identical hash values. However, the probability of collision in the SHA-256 algorithm is about 10-76.
In theory, it is possible to guess the correct hash value using a brute-force attack. But in practice, such a hack will require an inadequate amount of time.
There are more reliable methods of protection, but they are more expensive. In this project, the team and the customer concluded that the SHA-256 algorithm provides a sufficient level of security.
The Scope of Work
- Enhancing the functionality of the desktop application
- Licensing service design and development
- Web application development
- Communication protocols development
Technologies Used
- The web application was developed in Java using the Jmix framework.
- The desktop application was developed in C++ using the Qt framework.
- The SHA-256 hashing algorithm was used as an encryption method in the project.
Result
The Integra Sources team created a licensing system for 3D printers that allows the product to be distributed by subscription. We improved the previously created desktop application so that it can be used for activating devices. The team also developed a Jmix application for generating and storing licensing keys, license data, and other information.
The customer has already launched mass production and attracted the first customers. The product has proved to be in demand, and the company expects to take a significant market share in the coming years.
The solution allowed the customer to:
- Start distributing the product by subscription, offering each client the most suitable set of functions for the required period of time, and create different pricing models for different categories of users.
- Provide the company with regular and predictable income and increase customer loyalty.
- Protect the product from unauthorized use.
- Start collecting product usage statistics to better understand the target audience and improve the product in the future.
Budget
Duration
You might also like...

Firmware Development for Augmented Reality Glasses
The team improved the customer’s firmware for augmented reality glasses by developing drivers for the displays, accelerometer, and gyroscope of the device. 
LEARN MORE 

Software for EEG System
The Integra Sources team developed energy-efficient embedded software and an SDK for a medical EEG system. We delivered robust data transfer and storage, implemented multitasking on FreeRTOS, and improved connection security. 
LEARN MORE 



